Do You Have a Security Failure in Your Cloud Communications Budget?

How Security as a Service eliminates your risk and protects your budget.
These days, data breaches are in the news on a weekly basis. They’re becoming more and more frequent, and they impact all types of organizations, big or small. While we often hear about data breaches happening to large retail stores, where credit data is compromised, other types of data can be at risk too, including communications data for organizations like yours.
Without adequate security, you’re at risk of data breaches, data loss, insecure APIs, account hijacking, and more. Security failures like these lose companies millions each year- they even put many companies out of business. In short, you need to secure your communications data. If you’re renewing your current communications contract or considering a new provider, it is crucial that security is part of your decision-making process. But first, you need to understand what you’re looking for. What kind of security do you need? How can your communications vendor help with security? And how is security even put into place?
The Actual Cost and Risk of a Data Breach
Before you can put adequate security in place, you need to understand the true risk of a data breach. This will help you understand what kind of security you need to protect your data.
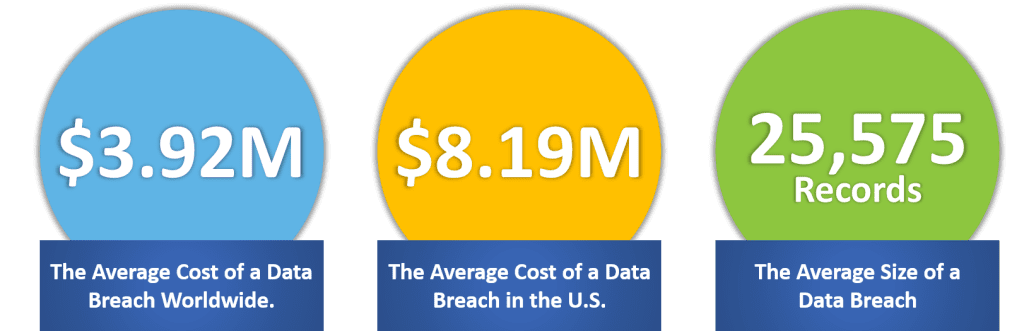
The average cost of a data breach worldwide is $3.92 million. The average data breach cost in the U.S. is $8.19 million. And the average size of a data breach is 25,575 records. These are scary numbers. But the cost of a data breach is more than a lump sum or record count. It affects every facet of an organization. To break it down, imagine a company with 200 employees that just got hacked- over 25,000 records were compromised. First and foremost, the company will likely be sued. This could cost the company $4 Million. On top of being sued, there will also be fines from the EU, which can be up to 4% of the company’s top-line revenue. To add insult to injury, the company’s customers and prospects are now concerned about the security of their confidential information; a recent study of data breaches in the UK found that a typical company loses about 2% of its value after a breach. Other studies have shown that loss of customers’ accounts for 36% of the cost of a data breach.

When your communications data lives in the cloud, it is subject to risk, purely because the data is accessible from many locations. And a data breach can cost you a lot. In fact, 26% of businesses will experience a major security threat in the next 24 months. And of those businesses, 60% of impacted small businesses will go out of business after a security breach. Adequate security mitigates your risk. That’s why it’s pivotal to select a cloud provider that considers the security offerings of their cloud solution to be a crucial service. Security isn’t something that they should be adding on- it should already be built into their communications packages.
Breaking Down Security as a Service
Security isn’t something that you need to purchase in addition to your cloud communications; good providers already include it in their services. In fact, if your current provider doesn’t include security, it is a red flag, and you shouldn’t renew with them. If a provider that you are considering doesn’t include security, then they should be immediately eliminated from your list of options. If your current or potential provider does deliver security, the way they deliver it is what matters. Security should be considered a critical piece of your cloud solution, and should be delivered as a service. A good way to understand Security as a Service is to compare it to buying or leasing a car. When you buy a car, just like you would buy a premise phone system, you are responsible for the car in entirety. You have to pay for the maintenance – the tire rotation, oil change, and any desired onsite security. When you select cloud communications, it’s more like you’re leasing the car. The leaser, or your cloud vendor, sets up a process for maintenance, updates, and security to the car as a service to you, and it’s all part of the cost of leasing the car.
In short, when it comes to cloud communications, security is already part of the package and cost. That being said, security is a crucial part of your cloud communications decision making process. You need to review each vendor’s security to see what they will deliver. After all, if you were to lease a car, you would take a look at what maintenance is included in the contract. Is the maintenance plan adequate to protect the car and extend its longevity? Or are you paying a lot for nothing? You need to guarantee that you have the right security in place to protect your communications data, so that you can relax and take full advantage of the cloud.
Defining Security is a Service
When you start evaluating the security delivered by your potential vendors, you need to understand what you’re looking at. What does security mean in the cloud? How can your cloud vendor implement a service that will mitigate your risk? Security is broken down as much by what it is not as by what it is:
Security Is Not a Wall
Many individuals believe that security is an objective to obtain, as simple as putting a virtual wall up around their data. It’s not. If you build a wall, someone will simply find a way to defeat it.
Security Is Not a Feature
Security shouldn’t be confused with features. Features are things like encryptions, SRTP, passport management, policy enforcement, and standards adherence.
Security Is a Process
Security is an ongoing process that requires continual attention and focus. It demands an active effort and should be continuously reviewed, assessed, and improved upon. Security is making sure the right protection is in place, then testing it, reviewing it, and iterating on it, indefinitely.
Instead of These Features…
- Encryption
- SRTP
- Password Management
- Policy Enforcement
- Standards Adherence
Use These Processes
- How often is the software updated?
- Who is monitoring it?
- Is there penetration testing?
- How often?
- Who responds to a security issue?
Now that you understand the value of security and what Security as a Service means to you, you can begin evaluating your potentials vendor’s security. Evaluating the security of your cloud vendor is a crucial part of your decision making process.
Evaluating Security as a Service
Asking your current or potential cloud communications provider if they offer Security as a Service isn’t enough. You also need to review the inclusions, processes, and activities that they implement. To start, review their security documentation. This will help you know exactly what services your vendor will provide on your behalf. At minimum they should provide documentation on:
- Members of the Security Team
- Penetration Testing
- Quick Turn-Around Security Patches
- Certification Review
- Published Security Plans
- Toll-Fraud Monitoring
- Real-Time Response
- Active Monitoring
It’s also important to review the security certifications that your vendor has acquired. Depending on your industry, you may require different security certifications for your data, including HIPAA, FISMA PCI, etc. Your cloud communications provider should have a list of security certifications that they have. Certifications evolve and change over time and are a process. There is the initial certification, refreshing the certification, and certification change. Not only does your vendor need to have the certifications your business requires, but they must also have a continuous process in place for maintaining and adding certifications.
Verifying Your Vendor’s Security as a Service
Now you know what to look for in regards to Security as a Service, but how do you verify that your cloud communications vendor can deliver on their promises? Security is about commitment and delivering on a process and you need to make sure they can practice what they sell. To make sure that you have all of the information, dig into their security service by asking about the following topics:
Ask About Their Security Department
You need a full CV on their security department lead, and more. Make sure to find out who leads the department and what their expertise is. Learn how many people are on the team, what tasks they complete, and where they’re located.
Ask About Their Security Standards
You need to see the documentation to make sure their standards are in line with you needs. This will help you understand what their standards are based on. Look for the continuous process and learn who has access to the data (employees, contractors, third parties?). And finally, dive into how their data centers are secured.
Ask About Their Customer Security Services
You need to understand what services they will actually be offering. Are they monitoring logins? Are they monitoring calling activity? What’s their proactive response policy? Do they have a specific example of proactive response? How do they prevent security breaches? And how often are they releasing security updates?
Ask about Penetration Testing
You need to discover if they complete penetration testing, how often, what the surface area is (data centers, clients, and more), and who does the testing.
Ask about External Audits
Most certifications that your industry requires will require an external audit. These audits can be a good verification of their security services even if you don’t have a certification need. Make sure to ask for audits specific to your clients certification needs and check how recent the audit is.
To make sure you know what questions to ask and that you don’t miss any important pieces, use Vertical’s checklist “Does Your Cloud Vendor’s Security Measure Up?”. Click here to download the checklist. Security is important, but it doesn’t have to be scary. By evaluating security when you are considering your current or prospective cloud provider, you can ensure that you have all of the pieces to your communications solution. Understanding the ins and outs of your cloud provider’s security offerings, you can get a good idea of what to expect, and if it is enough to protect your data. Are you concerned about your current vendor’s security? Or do you need a cloud vendor who can provide best-in-class security? Vertical can help.



