Cyberattacks Are Scary, Disruptive, and Expensive… And Increasingly More Common

What Can You Do to Keep Your Phones Running Smoothly in the Face of an Attack?
In September, the telecommunication company Bandwidth.com lost $12 million during a cyberattack. Accent, RingCentral, Twilio, Dialpad, and Phone.com all reported outages due to the Distributed Denial of Service Attack (DDOS) attack.
Telecommunications was the number one segment experiencing DDOS cyberattacks in the first quarter of 2021, according to a Cloudflare survey. Trends show that the frequency of these attacks is increasing, having more than doubled since 2014.
When your VOIP phone service is down, it can be way more than a headache. At any moment, it may become your company’s #1 emergency. No incoming calls, no outbound calls. And who knows how long you’ll be down for? Business can come to a near-complete stop. Overall, between $20,000 and $40,000 is lost each hour from these DDOS attacks.
These attacks are global, originating all over the world, however companies in the USA are increasingly becoming target #1. In the most recent quarter, attacks against companies based in the US were double the next highest country.
If you have SIP trunks or a cloud telephony system, you don’t have to be targeted to be impacted. When a major carrier like Bandwidth.com goes down, you will likely be affected.
How do DDOS attacks work?
DDOS attacks target a network by overloading it with illegitimate requests. These requests either crash the server or block legitimate ones from being received in a timely manner. Think of it as a bunch of nefarious actors crowding a bridge, preventing anyone else from being able to pass.
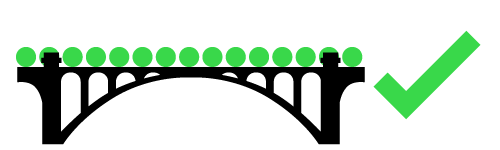
Normal traffic – Under normal conditions, traffic flows evenly and smoothly

Volume Based Attacks – a network’s bandwidth is saturated by the sheer volume of data

Protocol Attacks – the capacity of servers, firewalls, or load balancers is saturated by targeting its vulnerabilities
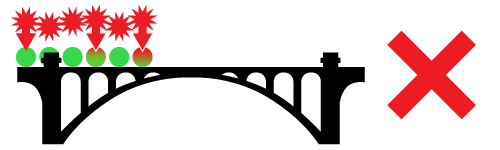
Application Layer Attacks – the application server is saturated with seemingly innocent traffic, blocking legitimate traffic
Any of these can take out your phone service, disable your chat, and block your video conferences. Choosing the right partner for your VoIP, UCaaS, or CCaaS services can be the difference between major suffering and only minor glitches. Start by looking for a company that stands behind its cloud communication security promises with a financially backed Service Level Agreement (SLA). If you have an outage, you’ll be reimbursed. The best motivator for a company to avoid outages is always monetary.
How do I choose a service that will protect me from DDOS?
Let’s break it down. Here’s what to look for when choosing a cloud telecommunication partner that won’t be brought to its knees by DDOS attacks.
1 Look at the organizational chart.
Is there a dedicated Network Operations team monitoring traffic? Is there a separate security team dedicated to protecting the infrastructure? How much experience do the people in these roles actually have defending cyberattacks?
2 While you’re at it, ask about their processes.
Having a team is a good start, but more important is their reaction to a DDOS attack. Have them tell you their response plan, even if it means signing an NDA to get the information. Remember it’s not enough to have a plan for current iterations of attacks. How will they respond to future threats? Look for a partner that has a living, developing defense.
3 Is the platform geographically redundant?
In other words, can one local disruption take down your entire service? If one location is attacked by a DDOS effort, your provider should be able to seamlessly transfer all your operations to another location. And do they have multi-cloud diversity— company-owned data centers in addition to leading cloud providers like Amazon and Oracle? This level of connectivity and resiliency is crucial for company communications… and customers demand it.
4 Do they have carrier redundancy?
Many cloud providers have their own phone service or use a single vendor to hook them up to the rest of the Public Switched Telephone Network (PSTN). This will become a point of failure in a DDOS attack. Look for vendors who partner with multiple carriers, not just for data, but for their voice connections as well.
5 Metrics, metrics, metrics.
Don’t trust promises of impenetrable infrastructure or unlimited server capacity unless they’re willing to show their work! Look for a company that provides real-time metrics and 24×7 observability of its network operations. Bonus if they have a public site providing a detailed status for monitoring network and service conditions. Like this.
8×8 is a great carrier that uniquely uses dozens of top-tier Public Switched Telephone Network (PSTN) carriers for redundancy in getting your calls out, even when a major player (like Bandwidth.com) is having an outage.
Conclusion
These 5 steps are key to finding the right provider—one that won’t falter in the face of the mightiest DDOS attacks that are only getting bigger and more intense. It’s hard to exaggerate the scale; Cloudflare recently identified a staggering 2Tbps DDOS attack, an unprecedented assault using an estimated 15,000 bots. If this seems overwhelming and you aren’t sure how to begin going through all these steps, Vertical Communications can help. Our expert staff brings 972 years of experience to bear. We will help you through the above evaluation steps so you can be supremely confident in your service and protection against attacks.



